
Adding constraints to the rules – practice
In this article we will practice modifying the constraint in the base module for the myapp_se program. First you take the type myapp_se_tmp_t into the mcs_constrained_type group, add the following statements to myapp_se.te file:
require { attribute mcs_constrained_type; }
typeattribute myapp_se_tmp_t mcs_constrained_type;
Then rebuild and reinstall the module myapp_se.
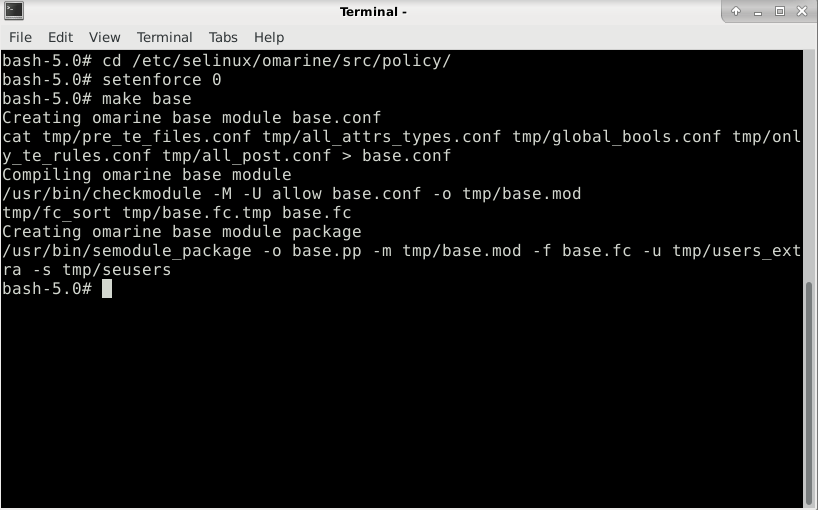
Next we create a base.conf file. Change to /etc/selinux/omarine/src/policy directory and switch to permissive mode, as the root user:
cd /etc/selinux/omarine/src/policy
setenforce 0
Generate the base.conf file. It is exactly the original file of the base source policy module:
make base
Next modify the base.conf file as shown in the previous article.
Now create the binary module file base.mod:
checkmodule -M -U allow base.conf -o base.mod
Create new base policy package base.pp:
semodule_package -o base.pp -m base.mod -f base.fc
Finally install the new base policy package base.pp as usual, then return to enforcing mode:
semodule -i base.pp
setenforce 1
Now root can no longer read /tmp/myapp_se.123456 file

Of course this only really makes sense when you adjust the policy to disallow root to switch to permissive mode. Then the permissive mode is only available when booting with the kernel command line parameter or modifying the configuration file /etc/selinux/config.